
What Is a Digital Signature? Learn How To Secure It
The advent of the software revolution has brought unprecedented productivity and convenience. However, it has also led to an increased threat in the form of hacking and data breaches.
Forging a signature is one of the oldest forms of fraud in the book and is probably the quickest way for a criminal to convince a legal or business institution that they’re someone they’re not. Thanks to digital signature security, we finally have a way to verify online activities.
What is a digital signature?
A digital signature is a cryptographic technique used to verify the authenticity of digital documents, messages, and transactions. It solves the problem of tampering, alteration, and impersonation. Digital signature security is maintained through asymmetric cryptography.
On the surface, the move from the traditional written signature to electronic signature software for conducting business seems to have made this malicious imitation easier than ever. After all, the physical artistry of crafting a signature was replaced with simple stylus strokes and images.
Luckily, this issue has been at the forefront of IT experts’ and e-signature software companies’ consciousness. Protection of identity and data is by far one of the most important parts of their business models.
Despite this, not all software solutions are created equal, so it will serve you well to develop an understanding of what security measures are necessary to defend your business and clients.
How digital signature works
At the core of all these forms of data security is the digital signature. A digital signature is separate from the normal e-signature in that it is not a representation of a ‘formal’ physical signature and is not used for notarizing business and legal agreements.
Instead, a digital signature is a security tool consisting of a complex mathematical algorithm used to verify the authenticity and validity of a message sent over the internet.
E-signature software makes use of digital signatures in order to provide increased security to its users. The basic function of this process is to provide two sets of digital “keys” for a document using what is known as the public key infrastructure system (PKI).
The first key is a public key that the sender of the document holds, while the second is a private key that is generated by the act of signing the document itself.
When the notarized document is returned to the original entity, the embedded cryptographic algorithm will compare the two keys. If the private key sent by the signee doesn’t match the public key held by the recipient, the document will remain locked.
This simple encryption process is nonetheless an extremely effective way to ensure that an electronic signature remains secure and that the records of deals and agreements made are accurate and reflective of the actual state of affairs for either a business or another legal entity.
Types of digital signatures
While the standard PKI system is generally more than enough for most businesses, some organizations work with extremely sensitive data and need extra layers of protection for the agreements they handle.
Certified signatures
Certified signatures are like typical electronic signatures in that they are used to notarize legal and business documents. However, they also include an additional level of security and assurance in the form of a digital certificate.
These certificates are issued by a third party known as a Certificate Authority (CA) and help the recipient verify the origin and authenticity of the document in question.
Approval signatures
Approval signatures function a little differently than other forms of electronic signatures.
In fact, they are not things that the final recipient intended to sign at all. Rather, they function to signify that a particular document has been approved by a particular person or entity so as to prevent unnecessary correspondence and optimize workflows and bureaucratic processes.
Invisible signatures
This form of digital signature allows a sender to transfer a type of document where the visual representation of a signature might not be appropriate while still verifying that it has been approved by the proper person (in the case of an approval signature) and/or had its authenticity certified.
The choice between providing a visible or invisible digital signature is generally decided by specific company policies and how much information you want to provide to a signee.
Classes of digital signatures
In addition to the various types of digital signatures, there are also specific tiers of digital security, ranked from least to most secure. The presence of specific security features may influence the ranking of a particular solution and are tied to the overall process of signature certification discussed above.
Class I
The first tier of digital signatures, class I signature certificates, provide a basic level of security and are generally only validated based on an email ID and username. Because of this, the signatures tied to this are not valid for legal documents or most business agreements.
Class II
The second class of digital signatures is often used for securing taxes and other financial documents and records where the risk and general security concerns are low or moderate.
Class II signatures function by comparing a signee’s identity against a secure database in order to help control who has access to what specific information.
Class III
The third and final tier of digital signature security comes in the form of online “checkpoints” that require an organization or person to present a specific form of identification, such as a driver’s license, before they are able to sign the agreement or document in question.
This type of signature security is used for things such as court filings, e-ticketing, and other areas where a high level of security is required.
Digital signature security features
While these general concepts will certainly pay themselves back many times over the course of your career, sometimes you just need to evaluate a particular piece of e-signature software based on the nitty-gritty of the specifications.
Below is a list of different features related to document and signature security meant to help guide your search as you find ways to ensure the integrity of your data.
PINs, passwords, and codes
This first feature is by far the most basic and straightforward; however, its near ubiquitousness is a testament to just how effective it is as a base level of security and is itself deceptively complex.
By using a document that is protected by a password sent out by the document owner, you can help the signee know what they’re signing is genuine while preventing unwanted document tampering at the same time.
Cloud security
With much, if not all, of digital signature software being delivered under the Software as a Service (SaaS) model, it’s crucial to make sure you know what to look for when it comes to the security protocols that will be remotely deployed in order to protect your legal and business agreements by the vendor itself.
Understanding past security breaches, data loss, and other risks is crucial if you want to make the best choice possible for your organization. This can be done in a few ways.
First, you want to make sure that the vendor in question is using a strong cloud infrastructure, usually through a partnership with service providers such as Microsoft Azure or IBM SoftLayer. The benefit of this is that it ensures the baseline security infrastructure of a vendor meets the various regulatory requirements for top-of-the-line digital security.
The next piece of the puzzle comes in the form of understanding the way in which the software vendor approaches data encryption. For this, there are two key terms you need to understand:
- Resting Data: Data that is kept in a cloud server or on a hard drive that isn’t currently being accessed by a program.
- Transit Data: Data in transit refers to the movement of data between servers and applications.
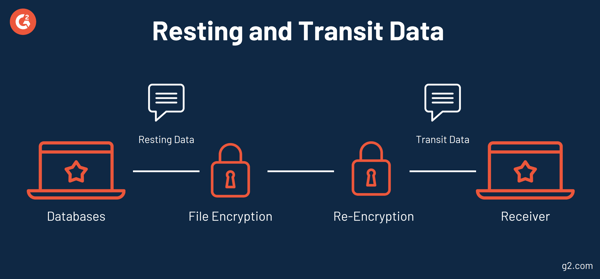
In order to have truly comprehensive cloud security, you need to ensure that the vendor you’re considering has strong data encryption both during the rest and transit phase of the data lifecycle. This will help protect current deals and agreements as well as ensure the security of records and documentation.
User authentication
Another way to quickly and effectively ensure an additional layer of security for your documents and agreements is to implement features to help verify the identity of the intended signee.
These features include tools to authenticate a signee before they execute their electronic signature, as well as a method to tie that authentication to the overall e-signature record.
Ideally, a solution utilizing a good set of user authentication protocols will allow for multiple authentication methods such as remote ID and password authorization, email address verification, or document uploads such as a driver’s license or other official government documentation.
Timestamping
Timestamps are usually associated with certified signatures as a way to visually display the verification of a particular document or agreement.
The presence of a digitally authorized timestamp indicates that the contents of a file have been verified at a given time by a particular person or entity and have not changed since. These stamps are fetched and applied through an automated service that is associated with the digital signature certification process.
Embedded audit trial
The ability to independently verify and archive an electronic signature can provide a crucial layer of security for your business.
This process is achieved when a piece of e-signature software embeds the signature directly into the document itself, creating a self-controllable, portable record free from the influence of the original software vendor.
The overall effect of this is to ensure complete control over your records and documents so that a change in account with the vendor will not affect your ability to access records.
E-Sign compliance checklist
Now that you’ve developed an understanding of the security features you need in order to protect your data, the next step is to ensure your electronic signatures remain compliant with the various regulatory oversights of your organization or industry.
Certain legal requirements must be met for your electronic signature to function as a valid business process.
These are included in the United States E-Sign Act, which provides electronic signatures with their legal status.
- Intent to sign: Like with a traditional signature, this refers to the standard legal condition where a signature is only valid if all parties intend to sign.
- Consent to do business electronically: For an electronic signature to be considered legally binding, all parties must agree to sign in a digital format.
- Association of signature with the record: The next part of ensuring E-Sign compliance is to make sure that the software solution used for the notarization of the agreement keeps an associated record that reflects the process through which the signature was created.
- Record retention: The final part is to make sure that records are completely kept and able to be accurately reproduced by the software solution used to facilitate the signature.
Signing process for compliance audits
One of the most important elements for reducing risk to your organization comes in the form of compliance audits.
These are reviews performed by both internal and external entities in order to evaluate a business’ adherence to regulatory guidelines and requirements for their size, location, industry, and more.
As a part of these audits, companies are usually asked to provide detailed accounts for their business processes, including when a document was changed or accessed and by whom.
When it comes to using electronic signatures to conduct business, you need to make sure that the signing provided by your chosen software solution is able to give a detailed audit of the signing process itself. This will show how a customer or business partner completed a business interaction over the internet and satisfy the agreements of your own business audit.
Related: Looking for more information about compliance? G2 Track can help you ensure your organization is above board when it comes time for an audit to be performed.
This may not be necessary if your company does not fall under regulatory oversight. However, if you do, you’ll want to make sure you have all of your bases covered when it comes to compliance.
Signed and secured
Regardless of the business you plan on conducting, the security concerns of electronic signatures can be easily offset by a prudent selection of a software solution that meets the unique organizational and industry requirements of your enterprise.
Following the above compliance checklist and understanding the different security features will have you well on your way to understanding exactly what you need to manage any and all risks.
Looking for more information on how to protect your data? G2’s guide on cybersecurity will arm you with all the knowledge you need to keep your information secure.